Introduction
Data security has grown to be of utmost importance to all people in the rapidly changing technological world, including private individuals, businesses, and governments. The secrecy, integrity, and validity of sensitive information are crucially dependent on cryptography. Despite their importance, cryptographic errors continue to pose serious hazards to data security. Numerous widespread cryptographic errors that make systems vulnerable to assaults have been found by the Open Web Application Security Project (OWASP). In this blog, we will examine these errors, emphasise their ramifications, and talk about ways to reduce these risks while boosting overall cryptographic security.
Inadequate Key Management
Secure key management procedures are essential to a strong cryptographic system. A complete cryptographic infrastructure can become exposed if the key creation, storage, distribution, and rotation processes are not appropriate. The use of secure key storage techniques, cryptographically robust random number generators, and well-specified key distribution procedures are all stressed by OWASP. Negligence in these areas may result in key compromises, which would allow attackers to counterfeit digital signatures or decode sensitive data.
Weak Encryption Algorithms and Modes
For protecting data secrecy, selecting the appropriate encryption methods and modes is essential. DES and MD5 are two examples of outdated or weak algorithms that are vulnerable to numerous cryptographic attacks. Data leakage and pattern recognition can also result from poor usage of encryption modes, such as Electronic Codebook (ECB) mode. Using AES and secure modes like Cypher Block Chaining (CBC) or Galois/Counter Mode (GCM) along with current, commonly used algorithms is encouraged by OWASP.
Insecure Cryptographic Protocols
Cryptographic protocols, such as SSL and TLS, provide secure communication over networks. However, improper configuration or utilisation of these protocols can introduce vulnerabilities. OWASP highlights issues like weak cypher suites, certificate validation errors, and protocol downgrade attacks as common pitfalls. It is crucial to follow OWASP’s recommendations for secure configuration, keep protocols up-to-date, and regularly audit and monitor cryptographic implementations.
Insufficient Cryptographic Strength
The strength of cryptographic primitives directly impacts the security of a system. Insufficient key sizes, weak password hashing algorithms, and inadequate entropy sources can undermine the strength of cryptographic operations. OWASP advises using sufficiently long and random keys, employing slow and computationally intensive password hashing algorithms like bcrypt or Argon2, and ensuring high-quality entropy sources to resist brute-force and precomputation attacks.
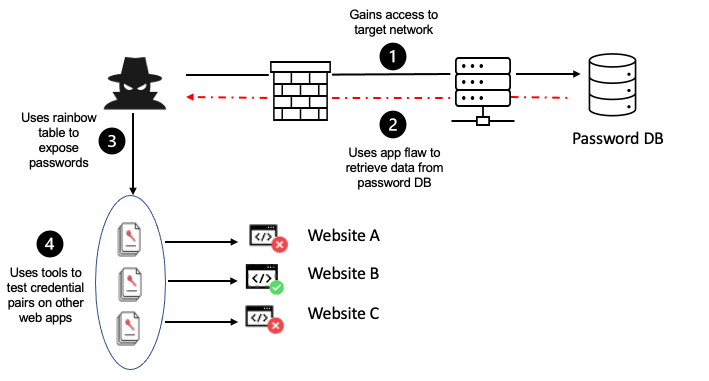
Insecure Cryptographic Storage
To prevent unauthorised access, data at rest must be safeguarded with cryptographic techniques. Storing sensitive information without encryption or using ineffective encryption technologies might result in data breaches and damage confidentiality. OWASP encourages the adoption of robust encryption methods and secure key management practises to safeguard data at rest, whether it is kept in databases, files, or other storage mediums.
Faulty Cryptographic Integration
Integrating cryptographic components into applications and systems is a complex task that demands careful attention to detail. Poor integration practices can result in implementation errors, such as incorrect usage of cryptographic libraries or insecure cryptographic APIs. OWASP stresses the importance of secure coding practices, cryptographic library selection, and independent cryptographic review to identify and rectify integration flaws.
Mitigation Strategies and Best Practices
To address these cryptographic failures effectively, adhering to best practices and adopting robust security measures are essential. The following strategies can significantly enhance cryptographic security:
- Stay Informed: Keep up with the latest cryptographic vulnerabilities and advancements by referring to resources like OWASP, NIST, and security forums. Stay informed about emerging cryptographic attacks and recommended countermeasures.
- Follow Standards and Guidelines: Implement well-established cryptographic standards and guidelines, such as those provided by NIST, the IETF, and OWASP. These standards undergo rigorous review processes and are continuously updated to address emerging threats.
- Regular Audits and Penetration Testing: Conduct regular audits and penetration testing to identify vulnerabilities and weaknesses in cryptographic implementations. Engage professional security firms or utilise open-source tools to assess the security posture of your systems.
- Secure Key Management: Implement secure key management practises, such as correct key production, storage, rotation, and dissemination. Make use of hardware security modules (HSMs) to store and manage cryptographic keys.
- Secure Development Lifecycle: Integrate cryptographic security into the software development lifecycle. Incorporate secure coding practises, perform security code reviews, and leverage automated security testing tools to identify and remediate cryptographic flaws early in the development process.
- Continuous Monitoring: Install a thorough monitoring system to keep an eye out for and respond to any unusual activity that may be impacting cryptographic operations. Watch the system logs, cryptographic protocol variables, and key use for any indications of a compromise.
Conclusion:
Understanding and correcting cryptographic failures is critical for securing sensitive information in an era of widespread data breaches and assaults. The OWASP Top 10 Cryptographic Failures is a useful resource that highlights the most common flaws that might jeopardise cryptographic security. Organisations may dramatically minimise the chance of cryptographic failures and increase their overall security posture by applying recommended best practises. The pursuit of cryptographic excellence is critical for adapting to emerging threats and ensuring data security in the digital era.