Introduction:
Developers make the mistake of not specifying the correct file permissions to the files while storing data for an application. These files are sometimes marked as world-readable and could be accessed by any other application without requesting permissions at all.
In order to check this vulnerability, all we need to do is go to the adb shell and then cd to /data/data/[package name of the app].
If we do a quick ls -l over here, we are able to see the file permissions of the files and folders:
# ls -l /data/data/com.aditya.example/files/userinfo.xml
-rw-rw-rw- app_200 app_200
22034 2013-11-07 00:01 userinfo.xml
Here, we could also use find in order to search for the permissions.
find /data/data/ -perm [permissions value]
If we do a cat userinfo.xml , it is storing the username and password of the application’s user.
#grep ‘password’ /data/data/com.aditya.example/files/userinfo.xml
<password>mysecretpassword</password>
This means any other application could also view and steal the user’s confidential
login credentials. This vulnerability could be avoided by specifying the correct
file permissions while developing the application, as well as properly hashing the
password along with a salt.
Example
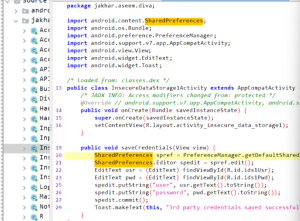
Install the DVWA (Damn Vulnerable Web Application) application on your device. We must use the Jadx tool, which is a DEX to Java decompiler, to analyse that programme. It can be used in both CLI and GUI to generate Java source code from Android DEX and APK files.
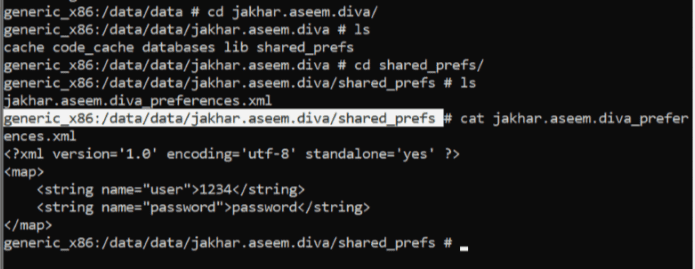
By studying code we notice that sharedpreferances folder is storing our input credentials.
Using adb shell command enter into the shell . go to data/data folder where all user installed applications are stored . Go to that particular application. Go to “shared_prefs” folder and read those sensitive details which are in .xml file
Conclusion:
Storing files in an insecure manner can lead to unauthorized access, data breaches, and loss of sensitive information. The consequences of insecure file storage can be severe, ranging from financial loss to damage to reputation and legal implications.
To ensure the security of file storage, it is essential to implement robust security measures.
Reference:
Insecure Data Storage: A Major Threat To Your Mobile App Security – AppSealing
For further clarifications or support, please write to contact@paradigmitcyber.com
