Introduction:
As web applications increasingly rely on RESTful APIs (Representational State Transfer), it becomes crucial to ensure their security and resilience against potential threats. Penetration testing, commonly known as “pen testing,” is a critical step in assessing the vulnerability of APIs. This blog will explore various techniques and tools for effectively testing RESTful APIs, providing practical examples along the way.
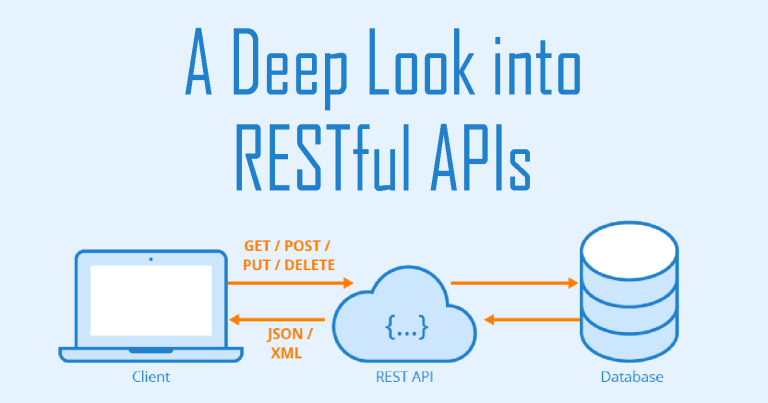
1.Understanding RESTful APIs:
Before diving into penetration testing, let’s quickly recap the key concepts of RESTful APIs. REST, as an architectural style, defines a set of constraints that enable systems to communicate over HTTP. RESTful APIs adhere to these constraints, making use of standard HTTP methods such as GET, POST, PUT, and DELETE to perform operations on resources.
2.Penetration Testing Objectives:
The primary objective of penetration testing is to identify vulnerabilities and potential security loopholes in a RESTful API. This process helps in detecting and mitigating risks before malicious actors exploit them. Here are a few key objectives to consider:
- Authentication and Authorization: Verify if access controls are implemented correctly, ensuring that only authorized users can access sensitive resources.
- Input Validation: Test the API’s ability to handle malicious input gracefully and prevent common vulnerabilities such as SQL injection, cross-site scripting (XSS), and cross-site request forgery (CSRF).
- Data Confidentiality and Integrity: Assess the API’s encryption mechanisms and ensure that sensitive data is transmitted securely and remains unaltered during transit.
- Error Handling: Validate how the API handles various error scenarios, ensuring that it doesn’t disclose sensitive information or leave the system in an unstable state.

3. Techniques for Testing RESTful APIs:
To conduct an effective penetration test on RESTful APIs, several techniques can be employed. Here are a few commonly used methods:
- API Fuzzing: This technique involves sending a large number of invalid, unexpected, or random inputs to the API to identify potential vulnerabilities.
- Injection Attacks: Test for injection vulnerabilities such as SQL injection and XML/XXE injection by manipulating input parameters and Analyzing the response.
- Security Headers: Check if the API is appropriately utilizing security headers such as Content Security Policy (CSP), Strict-Transport-Security (STS), and Cross-Origin Resource Sharing (CORS) to mitigate attacks like cross-site scripting and cross-site request forgery.
- Authorization Bypass: Attempt to access protected resources without proper authorization to identify any flaws in access control mechanisms.
- Rate Limiting and Throttling: Test how the API handles rate limiting and throttling, ensuring that it prevents abuse and denial-of-service (DoS) attacks.
4.Tools for Testing RESTful APIs:
There are several tools available to aid in penetration testing of RESTful APIs. Let’s explore a few popular ones:
- OWASP ZAP (Zed Attack Proxy): An open-source web application security scanner, ZAP provides features to test APIs for vulnerabilities such as injection attacks, broken access controls, and insecure communication.
- Burp Suite: A comprehensive web application testing tool, Burp Suite offers functionalities to analyze API requests and responses, manipulate parameters, and detect potential vulnerabilities.
- Postman: Although primarily known as an API development tool, Postman can also be used for testing APIs. It enables the creation and execution of test scripts, making it useful for functional and security testing.
- Nmap: While Nmap is primarily a network scanner, it can be utilized to discover open ports and services exposed by the API, providing insights into potential attack vectors.
5.Example Scenario:
To illustrate the penetration testing process for a RESTful API, let’s consider a fictional online banking API. Here are a few test scenarios:
- API Fuzzing: Send a wide range of unexpected inputs, including special characters and excessively large payloads, to test the API’s resilience against potential security vulnerabilities.
- Injection Attacks: Attempt SQL injection or XML/XXE injection by manipulating input parameters such as account numbers or transaction IDs to assess the API’s susceptibility to such attacks.
- Authorization Bypass: Try to access sensitive user data or perform transactions without proper authentication to identify any flaws in the API’s access control mechanisms.
- Error Handling: Manipulate input parameters to force the API to generate error responses and analyze how it handles and exposes these errors.
Conclusion:
Testing the security of RESTful APIs is crucial to safeguard sensitive data and prevent potential attacks. By employing techniques like API fuzzing, injection attacks, and thorough analysis of security headers, penetration testers can identify vulnerabilities and assist in strengthening the API’s security posture. Tools like OWASP ZAP, Burp Suite, Postman, and Nmap can significantly aid in the penetration testing process. However, it is important to note that API security is an ongoing effort, and regular testing and monitoring are necessary to ensure the API remains secure in an ever-evolving threat landscape.
Citations:
https://aws.amazon.com/what-is/restful-api/
https://www.redhat.com/en/topics/api/what-is-a-rest-api
https://www.smashingmagazine.com/2018/01/understanding-using-rest-api/
For further clarifications or support, please write to contact@paradigmitcyber.com
