The security researcher and investigators have found an open instance with more than 26 billion data records of many reputed companies, mostly compiled from previous breaches, although it likely also includes new data.
Organizations associated with these data records include:
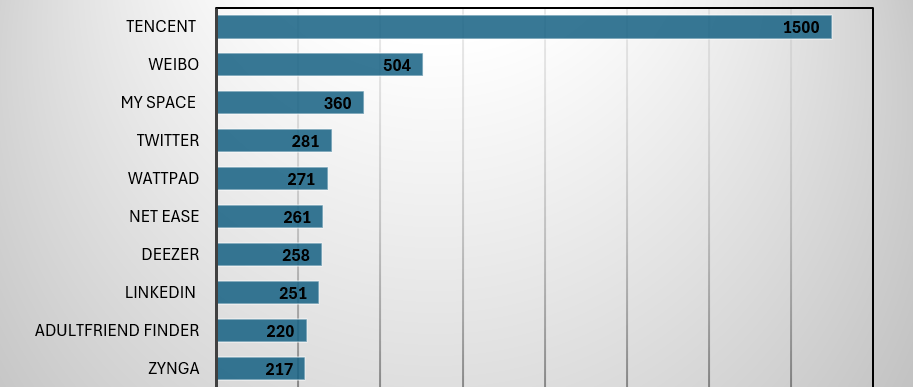
Here are the top-10 organization has the major data breach
| SNo | Organizations Name | Breached Records |
| 1 | 281 M | |
| 2 | Evite | 179 M |
| 3 | Wattpad | 271 M |
| 4 | NetEase | 261 M |
| 5 | Tencent | 1.5 B |
| 6 | Adult Friend Finder | 220 M |
| 7 | Zing | 164 M |
| 8 | My Fitness Pal | 151 M |
| 9 | VK | 101 M |
| 10 | Adobe | 153 M |
| 11 | JD.com | 142 M |
| 12 | Youku | 100 M |
| 13 | Badoo | 127 M |
| 14 | 504 M | |
| 15 | Canva | 143 M |
| 16 | My Space | 360 M |
| 17 | Deezer | 258 M |
| 18 | Zynga | 217 M |
| 19 | Luxottica | 206 M |
| 20 | 251 M | |
| 21 | Trello | 15 M |
| 22 | Dropbox | 69 M |
| 23 | Telegram | 41 M |
| 24 | Daily Motion | 86 M |
Most of the breached data is very sensitive and consists of passwords, usernames, Date of birth, credit cards, and email addresses. These consist of 26 billion records, 3800 folders, and 12TB of data. In total, 3,876 domain names were included in the exposed data set.
How serious is this?
- High danger of identity theft: With so much personal information accessible, criminals may quickly conduct sophisticated phishing attacks, steal financial data, and commit fraud.
- Social engineering schemes: Attackers can exploit your disclosed information to create personalized scams, winning your trust and potentially injuring you further.
- Targeted attacks: Hackers can use your information to gain access to other accounts, possibly compromising entire networks.
- Loss of faith: This breach reveals flaws in data security across various platforms, undermining user trust and raising worries about online privacy.
What’s the current situation?
- The origin of the breach and the party responsible are still unknown.
- Cybersecurity researchers are analyzing the leaked data to assess the full extent of the damage and identify affected individuals.
- Affected companies are notifying users and urging them to take precautionary measures.
- Authorities are investigating the breach and considering potential legal actions.
What can you do to protect yourself?
- Change your passwords immediately: Attempts of this sort will continue as long as password re-use remains common, and password reuse will remain common as long as people are expected to juggle an average of about 100 login credentials to navigate their modern lives. Very recent studies present disheartening numbers: about 60% of people can still be expected to reuse passwords, around 15% will use one password for absolutely everything they do online, and even the majority of IT professionals will email a password in plaintext on occasion. Annual “Top 10” lists of most-used passwords also continue to be strewn with “123” variations and the words “qwerty” and “password” modified just enough to meet website character requirements. Update your passwords on all potentially affected accounts, especially on those where you reuse the same password. Choose strong, unique passwords for each account.
- Enable two-factor authentication (2FA): Adding a second layer of security beyond your password makes it much harder for hackers to gain access.
- Beware of phishing emails and scams: Don’t click on suspicious links or open attachments from unknown senders. Be cautious about sharing personal information online and check the domain name and information in the mail.
- Monitor your accounts: Regularly check your accounts for unauthorized activity and report any suspicious behavior immediately.
How Paradigm IT Cyber Help our Users:
- Spear Phishing: Educate employees about the risks of spear phishing and provide regular training on how to identify suspicious emails, links, and attachments.
- SOC: monitoring your entire ecosystem and we generate alerts if any malicious activity is identified across multiple layers, which include endpoint, application, process, network.
- Shield:
- Phishing: how we prevent any malicious application / file [downloaded malware from emails] from running
- Data Exfiltration: This can occur through various methods, such as email, file transfer protocols, USB drives, or through exploiting vulnerabilities in the network.
- Cracked Applications: Cracked applications may be modified to include malicious code or malware, posing security risks to users’ devices and data.
- Cyber training is based on a case scenario so that we can help you learn how to avoid that type of scenario and how to secure your data.
For further clarifications or support, please write to ask@paradigmit.com

