In a rapidly evolving landscape of digital threats, the need for state-of-the-art cybersecurity infrastructure has never been more critical. However, sophisticated measures can’t do much, if you aren’t aware of your organization’s existing vulnerabilities and if your employees don’t have adequate training to identify treacherous human or non-human agents that might be actively contributing to a potential data breach. In this article, we will explore insider and external vulnerabilities that might act as “snakes within your network” and provide you with strategies to protect your digital assets from them.
Internal Threats vs External Threats to your Network
The first step to achieving more mature cybersecurity profiles is to understand the sources of threats to your data, and how equipped your organization is to deal with them. Cybersecurity threats can either originate as internal threats from within the organization or external threats that usually involve a form of malicious cyberattack from a hacker/cybercriminal to gain unauthorized access to sensitive information or disrupt operations.
SSH Snake — an External Threat
SSH Snake (aka Secure Shell Snake) is the most recent example of a malicious usage of a tool that can cause network-wide breaches. It is an ominous sign for organizations lacking the standards of security needed to tackle such emerging forms of external threats. On January 4, 2024, SSH-Snake was released on GitHub as a network mapping tool that is being used by external agents for criminal operations. In a way, SSH-Snake perfectly embodies the concept of “threats lurking like snakes in your network”.
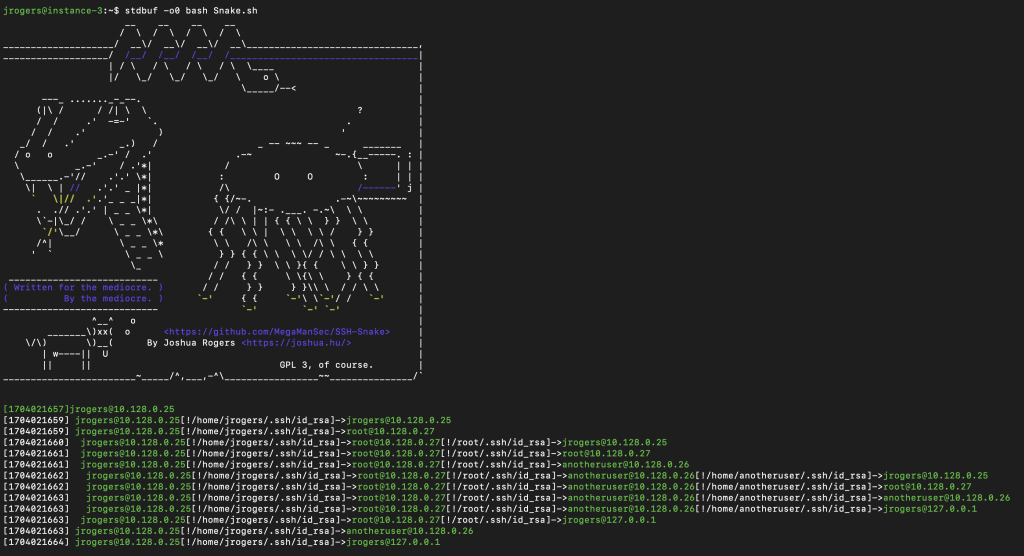
Traditional SSH worms seek to gain access to other systems on a network by accessing SSH credentials hosted on a compromised endpoint. However, the Sysdig Threat Research Team (TRT) discovered that the SSH Snake was more potent in its lateral movement through a network due to its enhanced ability to discover private SSH keys. According to the authors, it acts as a self-propagating, self-replicating, file-less script that can traverse private SSH systems while remaining virtually undetected by traditional anti-scripting measures.
This takes the SSH-Snake from a mere network mapping tool to a formidable state-of-the-art credential discovery weapon in the hands of cybercriminals. With over 100 victims who have had their private SSH keys and IPs exposed and exploited, it underlines the importance of businesses to invest in cybersecurity systems that are adaptive and proactive instead of being reactive.
Insider Threats — The Negligent and the Nefarious
Internal threats can arise from human error, employee negligence, or unverified contractors. Anyone with authorized access to your network without the awareness to stay vigilant against potential threats can trigger in a cyber incident. The reason why internal threats are particularly dangerous is that they can circumvent most layers of your cybersecurity infrastructure such as traditional perimeter defenses since they are caused by individuals with legitimate credentials.

Internal or insider threats can be broadly classified into two main types: The negligent and the nefarious. Negligent actions include password mismanagement, clicking on malicious links, human error, misconfiguration, or a general lack of awareness. Employees who don’t know better might become targets of phishing attempts and social engineering by criminals looking to weasel their way past network security measures. Using weak passwords that are stored on unsafe digital formats, oversharing to unauthorized parties, and not patching through security updates on time are all common examples of inadvertent acts of negligence that can compromise your organization’s network security.
Nefarious insider threats are caused by disgruntled employees or moles within your organization who have an agenda to engage in data theft or sabotage. They might be motivated financially or have a personal vendetta. Regular background checks and vulnerability auditing become a necessity as these bad actors can leverage their intimate knowledge of your security systems, protocols, and procedures to cause financial losses or reputational damage.
Vulnerabilities Exploited as Unforeseen Backdoors
It is said that the road to hell is often built with the best of intentions. On occasion, there is yet another class of “internal threats” that are vulnerabilities that were created as unintended consequences of other actions. These unforeseen backdoors are essentially a result of massive software security patches, software application updates, network infrastructure overhauls, rushed misconfigurations during deployment, or even a pattern of human behavior that is established as standard operating procedures within the organization.
If left unattended or undiscovered, these vulnerabilities can lead to zero-day attacks, resulting in massive losses or, even worse, the suspension of business operations.
Zoom — The Importance of Auditing Security Updates
If you think such exploits are far and few between, the case study of Zoom’s automatic update feature is a shining example that highlights the importance of performing thorough auditing of security updates. Back in November 2021, Zoom unrolled their automatic update feature for both Windows and Mac users along with a refurbished security update.
Skeptics such as Patrick Wardle who has had years of research experience with Mac security protocols decided to dive deeper into Zoom’s latest feature. He was able to uncover the fact that the automatic update feature had some fatal vulnerabilities in the code for its validation checks.

The first of them was a cryptographic signature check that was proven to be ineffective, inconsistent, and unreliable in verifying the true signatures of Mac users. This essentially meant that by merely refactoring certain packages, one could theoretically bypass the validation check and remain undetected. The second vulnerability caused Zoom’s updater module to accept any software that had passed the signature check.
The combined effect of these vulnerabilities meant that a hacker could feed an unstable version of Zoom through the auto-update module and open a door to completely gain access to the victim’s machine. On further investigation, it was revealed that this could be exploited to even inject spyware, ransomware, or other malicious software by merely triggering the Zoom installer to reinstall itself.
While these vulnerabilities were fixed in swift security patches, it is an important reminder to organizations around the globe to diligently audit security updates on many levels with a heightened focus on vulnerability testing. After all, enhancements in user functionality are often associated with a need for stronger security protocols.
Supply Chain Exploitation
The dangers of supply chain exploitation are often underestimated and deprioritized when creating cybersecurity systems. The potency of a supply chain attack that compromises systems and processes involved in distribution and production can’t be understated as it can impact an organization on multiple fronts. Threat actors use a targeted approach to leverage any vulnerabilities, blind spots, or weaknesses within an interconnected network of distributors and service providers to infiltrate past cybersecurity defenses. Once the incident happens, the attackers can expose sensitive information, disrupt operations, compromise product integrity, or use the system to create further weaknesses that can avalanche into broader cyberattacks against downstream targets.

A popular example of this is to let ransomware or worms piggyback third-party services through vendor channels that have access to critical systems or data within the organization. They may then exploit weak security controls within these blind spots to gain credentials of these trusted entities and escalate their privilege levels up to root. This will enable the attackers to pivot laterally and amplify the impact of the event with each subsequent system they target.
The final draft of the NIST CSF 2.0 that was recently released also sheds light on the importance of governance functions in achieving adaptive readiness in handling attacks. These threats can be averted by adhering to recommended security compliance policies, assessing vendor risk before integration, regularly reviewing code for vulnerabilities, and implementing top-down supply chain monitoring for enhanced threat visibility.
Safeguarding your Systems from Snakes and Security Threats
As with most things in life, it is always better to invest in proactive prevention than retrospective remedies. The following are our recommendations for achieving higher levels of threat protection:
- Early detection of threats through comprehensive Vulnerability Assessment & Penetration Testing (VAPT) paired with advanced Security Information & Event Management (SIEM) solutions can ensure effective risk mitigation and robust incident response.
- End-to-end endpoint encryption is a vital security measure against exfiltration attempts on confidential data. Remember: The cost of reliable cybersecurity is minimal compared to the cost of a data breach and hence isn’t an area where you want to cut corners.
- Your organization is only as safe as your weakest links. Therefore, ensuring that employees are competent enough to act as a resilient first line of defense against cyber threats is an absolute necessity. Investing in educating employees on best password practices and training them to tackle common threats through phishing and breach simulations can raise awareness and cultivate a culture of security-conscious employees.
Trust ParadigmIT Cyber with your Cybersecurity Needs
Our industry experts have extensive experience in identifying vulnerabilities and offering reliable recommendations to protect your organization against emerging threats while minimizing downtime at an affordable cost.
We also offer industry-specific Cyber Training & Awareness services to help you better protect sensitive data, safeguard against attempts at fraud, understand the depth of insider threats, and actionable measures to mitigate risks that could impact business operations. Proactive protection is the key to peace of mind.
Reach out to us today to get a quote for a panoramic VAPT and product demos. Contact Email: support.cs@paradigmit.com

