Introduction:
API security is a critical aspect of any application, and developers must be aware of potential vulnerabilities that can be exploited by malicious actors. One such vulnerability is Server-Side Request Forgery (SSRF), which allows attackers to send unauthorized requests from the server to other internal resources or external systems. In this blog post, we will explore how to test, perform, and exploit API7:2023 Server-Side Request Forgery using the Postman tool and Burp Suite.
What is API7:2023 Server-Side Request Forgery?
API7:2023 Server-Side Request Forgery is a vulnerability identified in the OWASP API Security Top 10 list. It refers to the ability of an attacker to manipulate the server into making requests to unintended resources, often leading to unauthorized access or data leakage.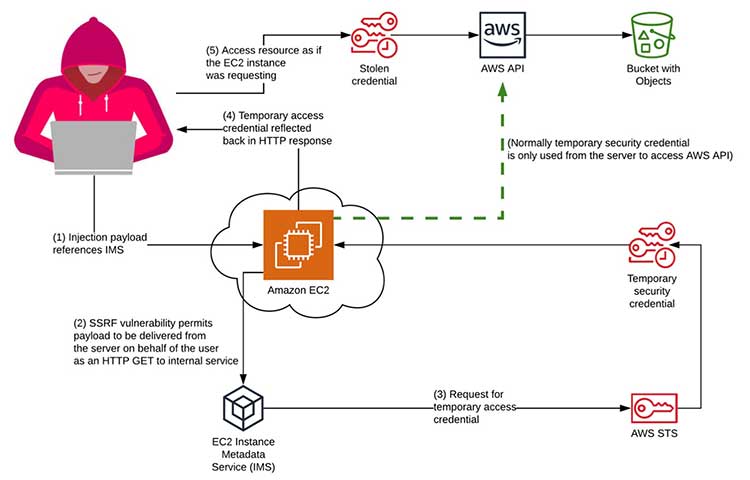
Testing for SSRF using Postman:
To begin testing for SSRF, we’ll be using Postman, a popular API testing tool. Follow the steps below:
Step 1: Identify the vulnerable endpoint.
Identify an API endpoint that accepts a URL parameter and seems to make requests to external resources.
Step 2: Prepare the payload.
Create a malicious payload that tricks the server into making a request to an unintended resource. For example, we can try providing “https://paradigmitcyber.com” or “http://internalserver” as the parameter value.
Step 3: Send the request.
Send the crafted request to the vulnerable endpoint and analyze the response. Look for any indications that the server attempted to make a request to the provided URL.
Exploiting SSRF using Burp Suite:
Now that we have identified a potential SSRF vulnerability using Postman, let’s move on to exploiting it with the help of Burp Suite, a powerful web application security testing tool.
Step 1: Configure Burp Suite
Configure Burp Suite as a proxy to intercept requests and responses between the target application and the server. Ensure that the browser or Postman is configured to use Burp Suite as the proxy.
Step 2: Intercept the request.
Send the same malicious request that was tested with Postman. Burp Suite will intercept the request.
Step 3: Modify the request
Within Burp Suite, modify the intercepted request and change the URL parameter to the desired target or resource you want the server to make a request to. This could be an internal network resource or a vulnerable third-party server.
Step 4: Forward the modified request.
Forward the modified request to the server and observe the response. Check if the server is making requests to the intended resource.
Preventing SSRF:
Now that we have demonstrated how to test and exploit SSRF vulnerabilities, it’s crucial to discuss preventive measures to secure your APIs:
- Input validation and whitelisting: Implement strict input validation to only allow trusted URLs and prevent unauthorized access.
- Secure coding practices: Avoid using user-supplied URLs directly in requests and perform thorough validation and sanitization of input.
- Use a web application firewall (WAF): A WAF can help detect and block malicious requests, including those attempting to exploit SSRF vulnerabilities.
- Network segregation: Separate internal resources from external systems to limit the potential impact of SSRF attacks.
- Regular security audits: Conduct periodic security audits to identify and address any potential SSRF vulnerabilities.
Conclusion:
Server-Side Request Forgery (SSRF) is a serious API vulnerability that can lead to unauthorized access and data leakage. By leveraging tools like Postman and Burp Suite, developers and security professionals can effectively test, identify, and exploit SSRF vulnerabilities.
Citations:
https://owasp.org/API-Security/editions/2023/en/0xa7-server-side-request-forgery/
https://salt.security/blog/api7-2023-server-side-request-forgery
For further clarifications or support, please write to contact@paradigmitcyber.com

