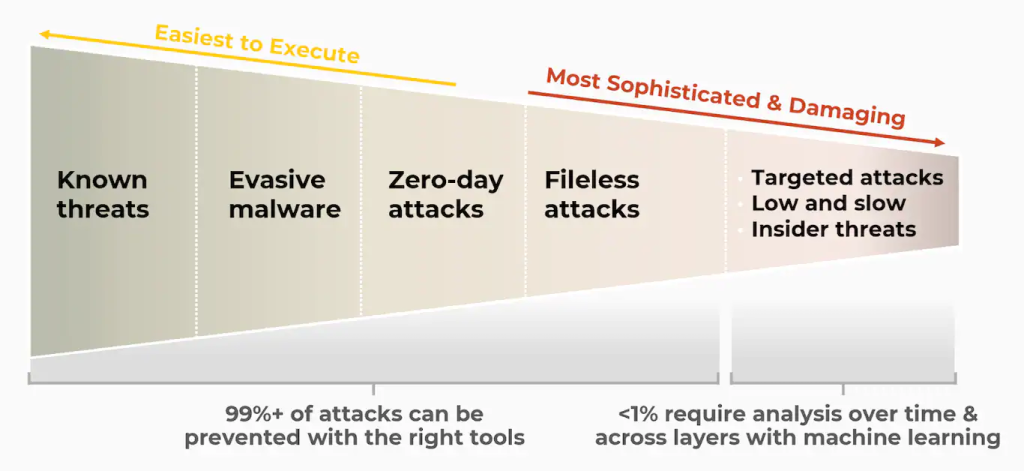
Organizations today receive a continuous barrage of attacks. These attacks range from simple, opportunistic attacks, such as a threat actor sending an email attachment with known ransomware in hopes that the endpoint is still vulnerable to the attack to a slightly more advanced attacks where threat actors might take known exploits or attack methods and attempt to hide them using evasion techniques such as running malware in memory.
If they are well-resourced, they might develop a zero-day attack that takes advantage of unknown app or system vulnerabilities. Fortunately, effective threat prevention tools can stop over 99% of all attacks automatically. They can apply multiple analysis engines, from the reputation of the source and the signer of a file, to the byte code distribution to the functions in an executable to block the attack. Since many zero-day attacks use known techniques, the right security tools can stop these zero-day attacks even if they have never seen a specific attack before.
However, the most sophisticated and potentially damaging attacks require detection and response. These attacks, such as insider threats, low and slow attacks, and advanced persistent threats, may require manual verification from a security analyst. Oftentimes, the only way to identify these attacks is by analyzing activity over time and across data sources with machine learning.
Security teams need EDR solutions to find, investigate and stop them.
Endpoint detection and response solutions collect, record, and store large volumes of data from endpoint activities to provide security professionals with the comprehensive visibility they need to detect, investigate, and mitigate advanced cyber threats.
How Does EDR Work?
EDR security solutions record the activities and events taking place on endpoints and all workloads, providing security teams with the visibility they need to uncover incidents that would otherwise remain invisible. An EDR solution needs to provide continuous and comprehensive visibility into what is happening on endpoints in real time.
An EDR tool should offer advanced threat detection, investigation and response capabilities — including incident data search and investigation alert triage, suspicious activity validation, threat hunting, and malicious activity detection and containment.
The Importance of EDR Security
The primary functions of an EDR security system are to:
- Monitor and collect activity data from endpoints that could indicate a threat
- Analyze this data to identify threat patterns
- Automatically respond to identified threats to remove or contain them, and notify security personnel
- Forensics and analysis tools to research identified threats and search for suspicious activities.
As remote work becomes more common, strong endpoint security is an increasingly vital component of any organization’s cybersecurity strategy. Deploying an effective EDR security solution is essential to protecting both the enterprise and the remote worker from cyber threats.
EDR is designed to go beyond detection-based, reactive cyber defense. Instead, it provides security analysts with the tools that they need to proactively identify threats and protect the organization. EDR provides a number of features that improve the organization’s ability to manage cybersecurity risk, such as:
- Improved Visibility: EDR security solutions perform continuous data collection and analytics, and report to a single, centralized system. This provides a security team with full visibility into the state of the network’s endpoints from a single console.
- Rapid Investigations: EDR solutions are designed to automate data collection and processing, and certain response activities. This enables a security team to rapidly gain context regarding a potential security incident and quickly take steps to remediate it.
- Remediation Automation: EDR solutions can automatically perform certain incident response activities based upon predefined rules. This enables them to block or rapidly remediate certain incidents and reduces load on security analysts.
- Contextualized Threat Hunting: EDR solutions’ continuous data collection and analysis provide deep visibility into an endpoint’s status. This allows threat hunters to identify and investigate potential signs of an existing infection.
Endpoint Detection and Response (EDR) Benefits :
- Greater security, EDR allows for the management of a large number of endpoints.
- Advanced threat detection. EDR fights emerging, unknown threats.
- More visibility. EDR provides context, information about the process of the attack, and information about its propagation. It provides the information needed to investigate forensic teams.
- Enables proactive detection. EDR is not limited to detection, it also looks for abnormal, suspicious patterns of activity. It thus contributes to a better security strategy.
- Automation: The EDR is highly automated and operates in real time. As we know, the faster the system, the more effective it is. EDR agents are installed on all terminals, allowing investigations to be launched quickly.
- The agent is lighter, and thus becomes less resource-intensive.
In short, It detects, investigates, and remedies.
Our EDR tool Benefits :
- Reduce time and effort spent investigating false positives
- Leverage whitelisting, blacklisting, and configurable security rules to achieve proactive security
- Centrally deploy and manage agents across thousands of endpoints in minutes and with minimal configuration efforts
- Adopt different levels of security based on the type and purpose of endpoints
- Protect ATM kiosks, point of sale systems, medical devices, and general-purpose systems
- Securely lock down legacy desktops and servers that run unpatched software
ParadigmIT Cyber provides EDR solutions :
The paradigmIT EDR tool is an Xtended ZeroTrust Platform is a cloud-based, SaaS-delivered, software-defined platform for hybrid networks that natively integrates Zero Trust access, endpoint protection and identity-based segmentation in a single platform, to simplify the adoption of Zero Trust and accelerate the enterprise journey to full cloud and multi-cloud.
References:
Anti-virus or EDR? understanding the differences and their advantages – TEHTRIS
For further clarifications or support, please write to contact@paradigmitcyber.com

