Introduction:
API4:2023 Unrestricted Resource Consumption, also known as “Resource Exhaustion” or “Denial-of-Service (DoS),” is a critical vulnerability that can impact the availability and performance of an API. In this blog post, we will delve into the process of testing, performing, and exploiting this vulnerability using popular tools like Postman and Burp Suite.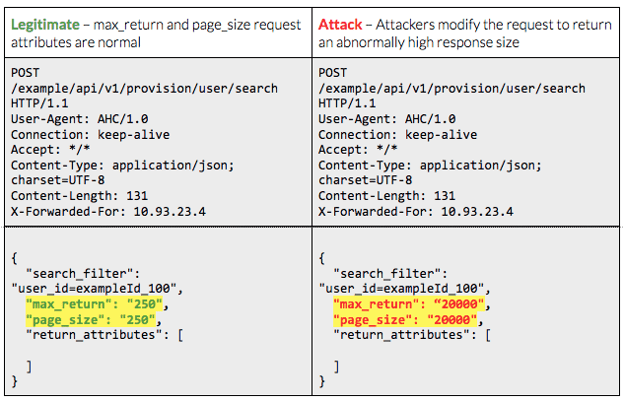
Testing Setup:
To begin, we need a testing setup comprising an API endpoint that exhibits the vulnerability we want to exploit. Let’s consider a simple e-commerce API that provides a search functionality. We will assume that this API has a vulnerability where it does not limit the amount of data returned in response to a search query.
-
Setting Up the API Endpoint:
In this example, let’s assume the search endpoint is: “` GET /api/search “` Ensure that the API is running and accessible for testing purposes.
-
Testing Tools:
For this demonstration, we will utilize two popular tools: Postman and Burp Suite. Postman allows us to construct API requests easily, while Burp Suite acts as a proxy to intercept and manipulate these requests.
Testing the Vulnerability with Postman:
Postman simplifies the process of crafting API requests and analysing responses. Follow these steps to test the API for unrestricted resource consumption:
- Open Postman and create a new request.
- Set the request method to GET and enter the API endpoint: `/api/search`.
- Craft a search query with many wildcards or a non-existent item to simulate resource-intensive requests.
- Send the request and observe the response time and data returned.
- Repeat the process with different variations of large or complex queries to assess the impact on system resources.
Analyzing and Exploiting the Vulnerability with Burp Suite:
Burp Suite is a powerful tool that allows us to intercept, modify, and analyze HTTP requests and responses. By leveraging its capabilities, we can gain deeper insights into the vulnerability and potentially exploit it further. Follow these steps to utilize Burp Suite:
- Configure Burp Suite as a proxy:
- Open Burp Suite and go to the “Proxy” tab.
- Ensure the “Intercept” option is enabled.
- Configure your browser or Postman to use Burp Suite as the proxy.
- Intercept the request:
- Make a search request in Postman.
- In Burp Suite, you will see the intercepted request in the “Proxy” tab.
- Right-click on the request and choose “Send to Repeater” to analyze and manipulate it.
- Analyze the request in Repeater:
- In the “Repeater” tab, you can modify the request parameters, including the search query.
- Experiment with different variations of queries to observe the impact on the API and system resources.
- Note the response time, server load, and any errors or anomalies observed.
- Exploiting the vulnerability:
- Craft requests that intentionally consume excessive resources, such as large search queries or highly complex filters.
- Observe the impact on the system, such as increased response time, server load, or potential errors.
- Document the behavior and gather evidence to support the identification of the vulnerability.
Conclusion:
Testing, performing, and exploiting the API4:2023 Unrestricted Resource Consumption vulnerability are essential steps in ensuring the security and reliability of APIs. By using tools like Postman and Burp Suite, developers and security professionals can understand the potential risks associated with unrestricted resource consumption and take appropriate measures to mitigate them. It is crucial to identify and address these vulnerabilities early in the development lifecycle to protect the API infrastructure and maintain a high level of service availability and performance.
Citations:
API4:2023 Unrestricted Resource Consumption – OWASP API Security Top 10 https://cyberw1ng.medium.com/understanding-unrestricted-resource-consumption-a-comprehensive-guide-2023-f5adcd9f7b18
For further clarifications or support, please write to contact@paradigmitcyber.com

