Introduction
API5:2023 Broken Function Level Authorization is a critical security vulnerability that can expose an application to unauthorized access and manipulation of resources. Testing for this vulnerability is essential to ensure the robustness of an application’s access controls. In this blog post, we will explore how to test, perform, and exploit Broken Function Level Authorization using popular tools like Postman and Burp Suite.
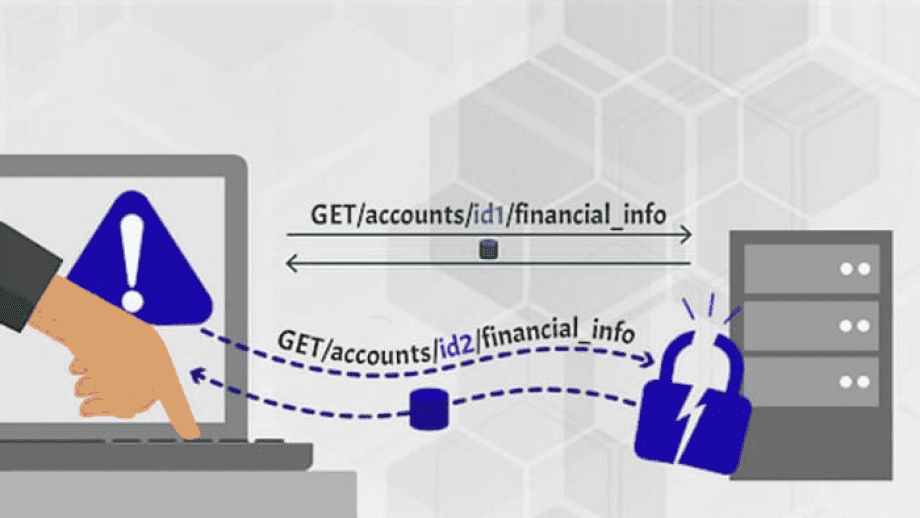
Testing Broken Function Level Authorization with Postman
Step 1: Identify the Target Endpoint
Identify the specific endpoint or function that requires authorization. In our example, we will consider an API endpoint: `/api/transfer` responsible for fund transfers.
Step 2: Authenticate and Obtain an Authorization Token
Use Postman to authenticate with the application using valid credentials. Once authenticated, the application will provide an authorization token that represents the user’s privileges.
Step 3: Test Unauthorized Access
Attempt to access the target endpoint without proper authorization. In Postman, send a request to the target endpoint using the obtained authorization token. Ideally, this request should result in an authorization error or denial.
Step 4: Observe the Response
Analyze the response received from the target endpoint. If the application fails to enforce proper authorization checks, the response may indicate a successful access attempt, even without the necessary privileges.
Exploiting Broken Function Level Authorization with Burp Suite
Step 1: Intercept the Request with Burp Suite
Configure your browser to use Burp Suite as a proxy and intercept the request to the target endpoint. This allows you to analyze and modify the request before it reaches the server.
Step 2: Modify Authorization Parameters
Using Burp Suite’s proxy, modify the request to include a higher level of authorization or access privileges. This modification could involve manipulating the authorization token or adding parameters that grant elevated privileges.
Step 3: Forward the Modified Request
Forward the modified request from Burp Suite to the server, bypassing the original authorization checks. The server may process the request, assuming the user has the necessary privileges, thereby exploiting the Broken Function Level Authorization vulnerability.
Step 4: Analyse the Response
Examine the response received from the server. If the request was successful and the server performed the unauthorized action, it confirms the presence of the Broken Function Level Authorization vulnerability.
Mitigating Broken Function Level Authorization
To mitigate Broken Function Level Authorization, follow these best practices:
- Implement Granular Authorization: Ensure that access controls are implemented and enforced at a granular level for each function or resource, based on the user’s role and privileges.
- Regular Security Testing: Conduct comprehensive security testing, including vulnerability assessments, penetration testing, and code reviews. Regularly test for Broken Function Level Authorization vulnerabilities to identify and remediate any issues.
- Input Validation and Sanitization: Implement robust input validation and sanitization techniques to prevent malicious input that could exploit access control vulnerabilities.
- Employ a secure API gateway that enforces access controls and validates requests before they reach the underlying APIs. The gateway should consistently enforce authorization rules across all functions and endpoints.
Conclusion
Testing and exploiting API5:2023 Broken Function Level Authorization is crucial for identifying and addressing vulnerabilities in an application’s access controls. Using tools like Postman and Burp Suite, developers and security professionals can simulate unauthorized access attempts and assess the robustness of the implemented authorization mechanisms. By uncovering and remedying these vulnerabilities, we can ensure the security and integrity of our applications and protect sensitive user data from unauthorized access.
Citations:
API5:2023 Broken Function Level Authorization – OWASP API Security Top 10
API5:2019 Broken Function Level Authorization – OWASP API Security Top 10
https://www.traceable.ai/owasp-api/broken-function-level-authorization
For further clarifications or support, please write to contact@paradigmitcyber.com

