Introduction:
SSL pinning, also known as certificate pinning or public key pinning, is a security technique used to enhance the trust and security of SSL/TLS connections between a client (such as a mobile app or web browser) and a server. SSL pinning is a way for apps to identify if they communicate with the intended server over HTTPS. This is done by verifying some parts of the SSL/TLS certificate keychain, usually the subjectPublicKeyInfo part.
-
Without SSL Pinning:
Your mobile app uses the device’s built-in list of trusted root certificates to check the server’s certificate in a standard SSL/TLS connection.
The server receives a request from the mobile app and replies with its SSL certificate, which also contains its public key. The mobile app compares the trusted root certificates kept on the device with the SSL certificate from the server. If a match is found, the connection is established safely. This strategy, meanwhile, is open to some assaults.
-
With SSL Pinning:
To mitigate potential attacks, SSL pinning is implemented.
The mobile app incorporates SSL pinning, which involves storing a specific SSL certificate or public key it expects the server to present.
Initially, the mobile app establishes a connection with the bank server without pinning. It receives the server’s SSL certificate. The mobile app extracts the server’s SSL certificate and identifies the public key or fingerprint associated with it. The mobile app pins the extracted public key or fingerprint, associating it with the bank server in its local storage.
When the mobile app communicates with the bank server, it checks if the presented SSL certificate matches the pinned public key it stored earlier. If the presented SSL certificate matches the pinned public key, the connection proceeds securely.
How to find an app that is SSL Pinned?
There are various ways to determine if an app is SSL Pinned and can broadly be categorized under static and dynamic analysis.
Static Analysis
It involves decompiling the app and analyzing the code and logic of the app by code.
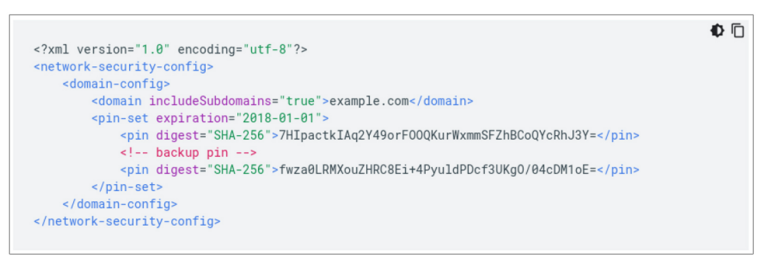
1. Check Pin Digest in the network_security_config.xml file
To find if an Android app has a network security config file, check for “android:network-SecurityConfig” in the Android Manifest file.

If it exists, then check for “pin-set” or “pin digest=” in the config file(usually exists at res/xml/network_security_config.xml)
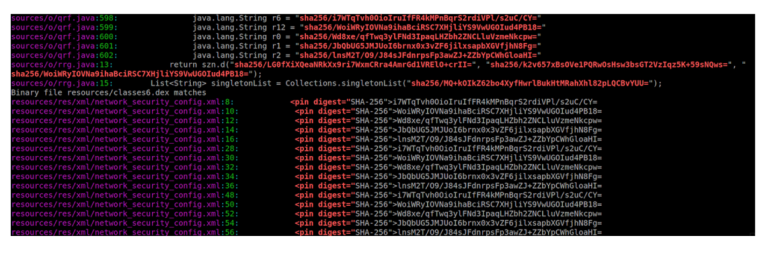
2. Grepping the Decompiled Source Code
If it’s a native app and can be decompiled to source code, there is another way to test SSL pinning. Using a simple grep over the source code will suggest to you if there’s any type of SSL pinning added to the app
grep -rni “<pin digest=\”\|CertificatePinner\.Builder(\|\.certificatePinner(\|sha256/[A-Za-z0-9\/+=]\{43,45\}”
Dynamic Analysis
It involves running the Android app and then analyzing the behavior of the app, network communications, etc.
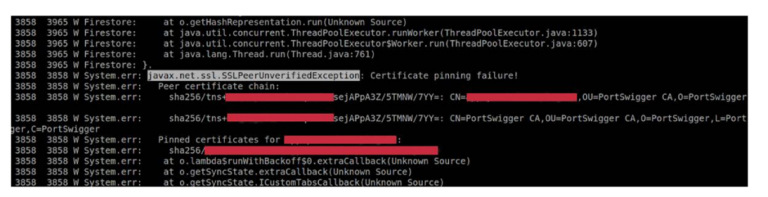
1. Proxy Error Logs
After you successfully set up HTTP(S) proxy with the mobile device, if you encounter a TLS negotiation error when using the app, then it’s an indication of SSL pinning.

2. Logcat Logs
It’s common for developers to log any errors (including SSL errors) in logs. In some cases, logs indicate SSL pinning some kind of SSL pinning with the app.
Bypassing SSL Pinning
Bypass SSL pinning varies with each app. If SSL pinning is the only security measure, the bypass may be a bit easier. Else another security measure like anti-tamper detection, root detection, etc will make SSL pinning bypass tougher.
1. Using a Lower Version of Android :
If an Android app employs SSL pinning and is compatible with a later version of Android, it might be possible to get around the security.
As an illustration, apps that use the Network Security Config file to store SSL certificate hashes can run on Android versions lower than Android N. Installing it in Android M (API level 23) and lower lets to escape SSL pinning since this pinning approach works for Android N and higher versions of Android.
2. Modification of Network Security config File :
By including “pin digest” in the Network security config file, SSL pinning may be accomplished with ease.
If the app only uses Network Security Config File for SSL pinning logic, removing the “pin digest” and recompiling the app can allow SSL pinning to be bypassed.
3. JustTrustMe – Xposed Module :
By turning off SSL certificate checks, the JustTrustMe Xposed module gets around certificate pinning. It might not always work. It merits a shot.
On your rooted device, install the Xposed framework. Install the JustTrustMe APK and allow Xposed Installer to use it. To completely enable, restart the gadget.
The JustTrustMe app replaces the functionality of common Android libraries’ SSL pinning implementations with hooks, allowing any SSL certificate.
4. Xposed Module – SSLUnpinning :
Android Xposed Module to bypass SSL certificate validation (Certificate Pinning).
5. Android-SSL-bypass
An Android debugging tool that can be used for bypassing SSL, even when certificate pinning is implemented, as well as other debugging tasks. The tool runs as an interactive console.
6. Frida CodeShare
The Frida CodeShare project is comprised of developers from around the world working together with one goal – to push Frida to its limits in new and innovative ways.
Bypassing Root Detection
frida –codeshare dzonerzy/fridantiroot -f YOUR_BINARY
Bypassing SSL Pinning
frida –codeshare pcipolloni/universal-android-ssl-pinning-bypass-with-frida -f YOUR_BINARY
Reference:
https://redhuntlabs.com/ultimate-guide-to-android-ssl-pinning-bypass/
For further clarifications or support, please write to contact@paradigmitcyber.com